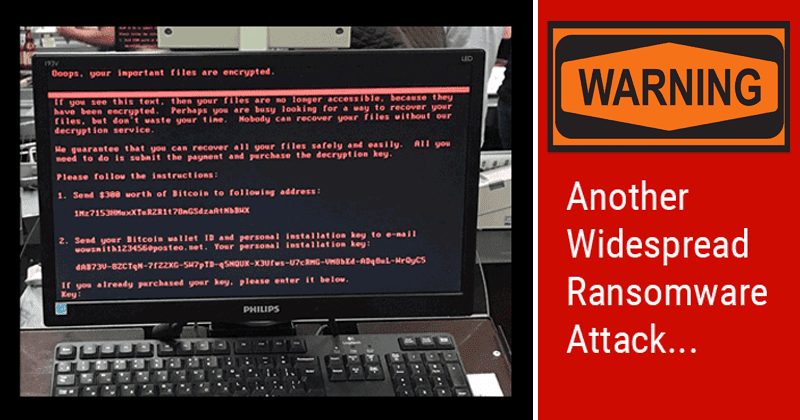
Security companies have been investigating this new global threat since early on, but ESET researchers have been able to figure out where it all began. This new ransomware, which seems to be a variant of “Petya” that in the case of being able to infect the Master Boot Record, ends up encrypting the entire hard disk, began to spread after the hackers had managed to compromise the MEDo management software, which is Widely used by Ukrainian companies. Based on the evidence (IoC’s) that are shared by various sources on the Internet and as it was also announced by ESET researchers, attacks using techniques harnessed by the recent WannaCry attack (vulnerability in SMB), use of emails with malicious attachments that resort Powershell, use of potentially dangerous tools (PsExec.exe), and other techniques for file and disk encryption. According to the information, the attack was done through an “infected update”, which allowed the attackers to launch a massive attack worldwide. ESET researchers have located the point from which this global epidemic has all started. Attackers have successfully compromised the accounting software MeDoc, popular across various industries in Ukraine, including financial institutions. Several of them executed a trojanized update of MeDoc, which allowed attackers to launch the massive ransomware campaign today which spread across the whole country and to the whole world. Even MeDoc has released a warning on their website as well. According to the latest information, ESET alerts users not to make any payment since the email account used by the attackers has already been blocked. According to Nuno Mendes, CEO of WhiteHat says that “We are again faced with a repeated phenomenon of massive cyber attacks that focuses attention on its final result which is a ransomware attack, where an astronomical number of machines and their data can be held hostage until the redemption value is paid (in the ‘best’ hypothesis Happens, and in the worst case the entire disk is encrypted)”. However, what stands out most from this new attack is the use of techniques previously used in other types of attacks that have been ingeniously composed to have a more devastating effect on systems. This or another wave of attacks can potentially be blocked proactively by implementing an anti-malware security solution with multi-layer protection (Cloud reputation service, HIPS rules for preventing application execution in temporary folders, advanced heuristic analysis, Web content filtering, anti-spam, memory-based malware detection, and so on) never neglecting to upgrade systems. As always, we will continue to track all relevant information about this computer attack that has already made thousands of victims by some international channels. So, what do you think about this? Simply share your views and thoughts in the comment section below.
Δ