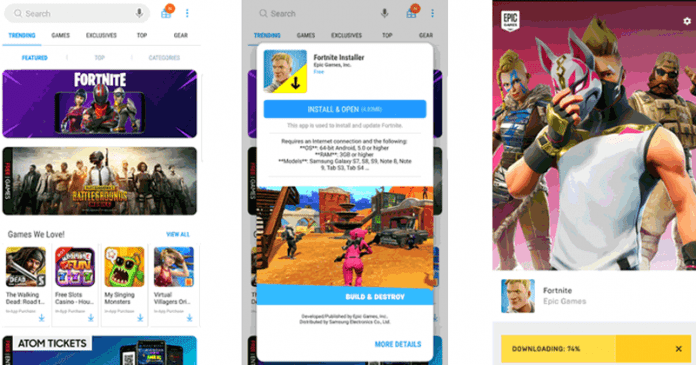
The flaw was discovered by the tech giant Google and seems to only affect the South Korean giant Samsung’s smartphones that have this game installed. Installing fake applications seems to be very straightforward with this flaw. The well-known and popular battle royale game Fortnite is the game of the moment, but the Epic Game choices for its distribution were not the best. By placing the game available outside the Google Play Store, players have to open the doors to installing software from external sources, which is not advisable. Now, as a result of a thorough evaluation of the tech giant Google itself, it has been proven that the Fortnite installer can be bypassed and used to install fake and external applications to this installer.
The disclosure of the flaw was made by an engineer of the tech giant Google and made public, and describes its simple form of exploitation.
Here’s the issue is explained on the tech giant Google’s Issue Tracker website:-
“The Fortnite APK (com.epicgames.fortnite) is downloaded by the Fortnite Installer (com.epicgames.portal) to external storage: dream2lte:/ $ ls -al /sdcard/Android/data/com.epicgames.portal/files/downloads/fn.4fe75bbc5a674f4f9b356b5c90567da5.Fortnite/ total 73360 drwxrwx–x 2 u0_a288 sdcard_rw 4096 2018-08-15 14:38 . drwxrwx–x 3 u0_a288 sdcard_rw 4096 2018-08-15 14:38 .. -rw-rw—- 1 u0_a288 sdcard_rw 75078149 2018-08-15 14:38 x1xlDRyBix-YbeDRrU2a8XPbT5ggIQ.apk -rw-rw—- 1 u0_a288 sdcard_rw 31230 2018-08-15 14:38 x1xlDRyBix-YbeDRrU2a8XPbT5ggIQ.manifest Any app with the WRITE_EXTERNAL_STORAGE permission can replace the APK immediately after the download is completed and the fingerprint is verified. This is easily done using FileObserver. The Fortnite Installer will proceed to install the substituted (fake) APK. On Samsung devices, the Fortnite Installer performs the APK install silently via the private Galaxy Apps API. This API checks that the APK is installed has the package name com.epicgames.fortnite. Consequently, the fake APK with a matching package name can be silently installed. If the fake APK has a targetSdkVersion of 22 or lower, it will be granted all permissions it requests at install-time. This vulnerability allows an app on the device to hijack the Fortnite Installer to instead install a fake APK with any permissions that would normally require user disclosure.” From what is seen, it will suffice for the attacker to change the name of the application to the same as that of Fortnite and the installation of software is done without any control. Epic Games has already responded to this problem and has even updated its application to circumvent this problem. Its CEO has also come out publicly to react to this finding, criticizing the tech giant Google for having publicly revealed it, so quickly. “Epic genuinely appreciated the tech giant Google’s effort to perform an in-depth security audit of Fortnite immediately following our release on Android, and share the results with Epic so we could speedily issue an update to fix the flaw they discovered. However, it was irresponsible of the tech giant Google to publicly disclose the technical details of the flaw so quickly, while many installations had been updated and were still vulnerable.” This is another point against the decision of Epic Games. If it was in the Play Store, these measures would probably have been evaluated earlier and the game would not be endangering the safety of the Samsung smartphone users. So, what do you think about this? Simply share all your views and thoughts in the comment section below.
Δ