The Tor network disguises your identity by moving your traffic across different Tor servers, and encrypting that traffic so it isn’t traced back to you. If you want to be anonymous — say, if you live under a dictatorship, you’re a journalist in an oppressive country, or a hacker looking to stay hidden from the government — Tor is one of the easiest ways to anonymize your traffic. And the best part? It’s free!
Querying Tor Metrics With Powershell
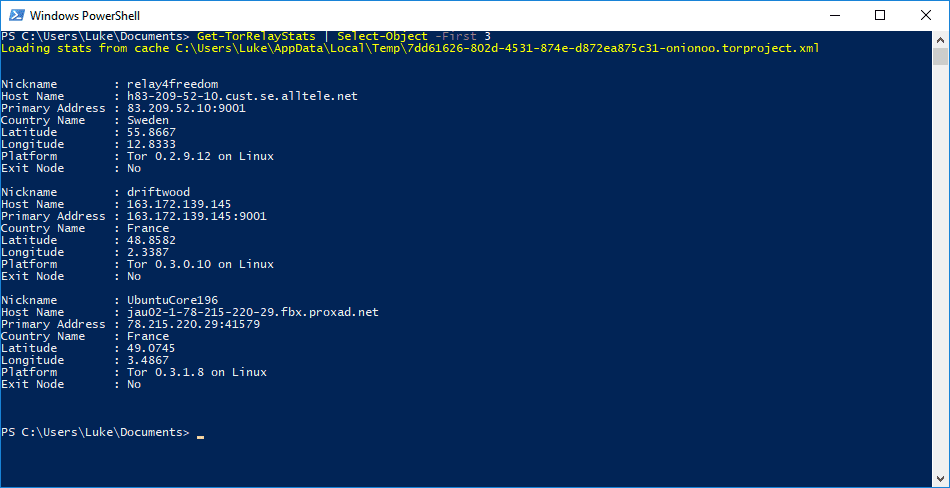
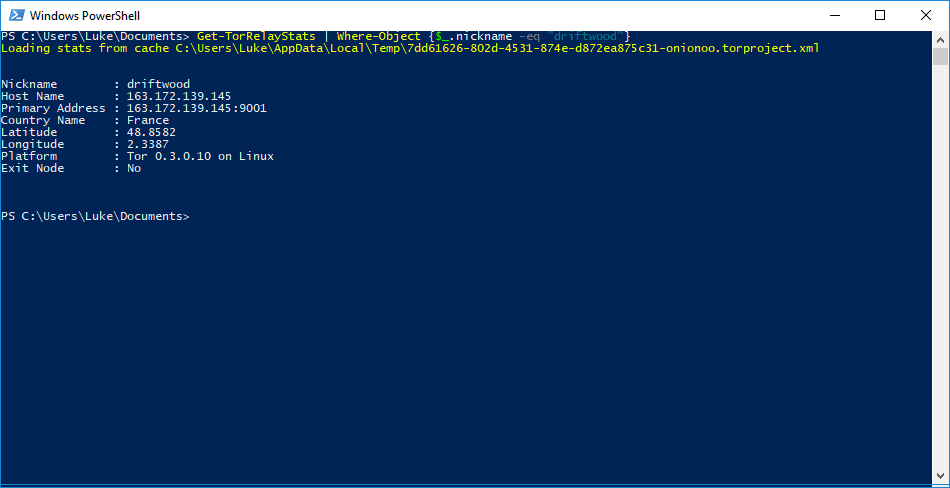
In the past there were very few ways for an inquisitive Tor user to find information about Tor relays nodes, the servers Tor routes traffic through, and bridges, alternate entry points that assist in bypassing filters that are designed to stop Tor use. To find out even the most basic information about a Tor relay node or bridge you would need to write your own script or application that queried the Tor Metrics database, or go on a wild goose chase trying to find a reliable source of information. Enter tormetrics.psm1, a new PowerShell module that collects Tor relay and node data via the Onionoo protocol and provides users a method of querying this data via the PowerShell command line. Created by Luke Millanta, widely known in the Tor community for creating OnionView, a web service which plots the location of Tor relay nodes onto an interactive map of the world, this module is an easy to use alternative to the days of old. The tormetrics module is available for download via Github Using the tormetrics module we can see that there are currently 8,108 Tor relay nodes and a further 2,687 Tor bridges. We are also, as shown here, able to view information about specific nodes or bridges:
“I would love to see people expand and improve upon this work. A few people have messaged me saying that they are using this module to achieve their own goals in separate projects. I look forward to seeing what they come up with!” Luke said. Written by Cameron Fisher
Δ