This new report, where the victim’s information was not disclosed, showed that it had a much higher outcome and consequences. The information states that it is a critical and sensitive structure in the United States, probably linked to the energy industry. The gateway to this attack was a company workstation, where the Triconex software was run, dedicated to industrial safety technology and created by Schneider Electric. After the knowledge of the attack, an alert was sent with safety recommendations for the entities that use Triconex.
Triton industrial malware
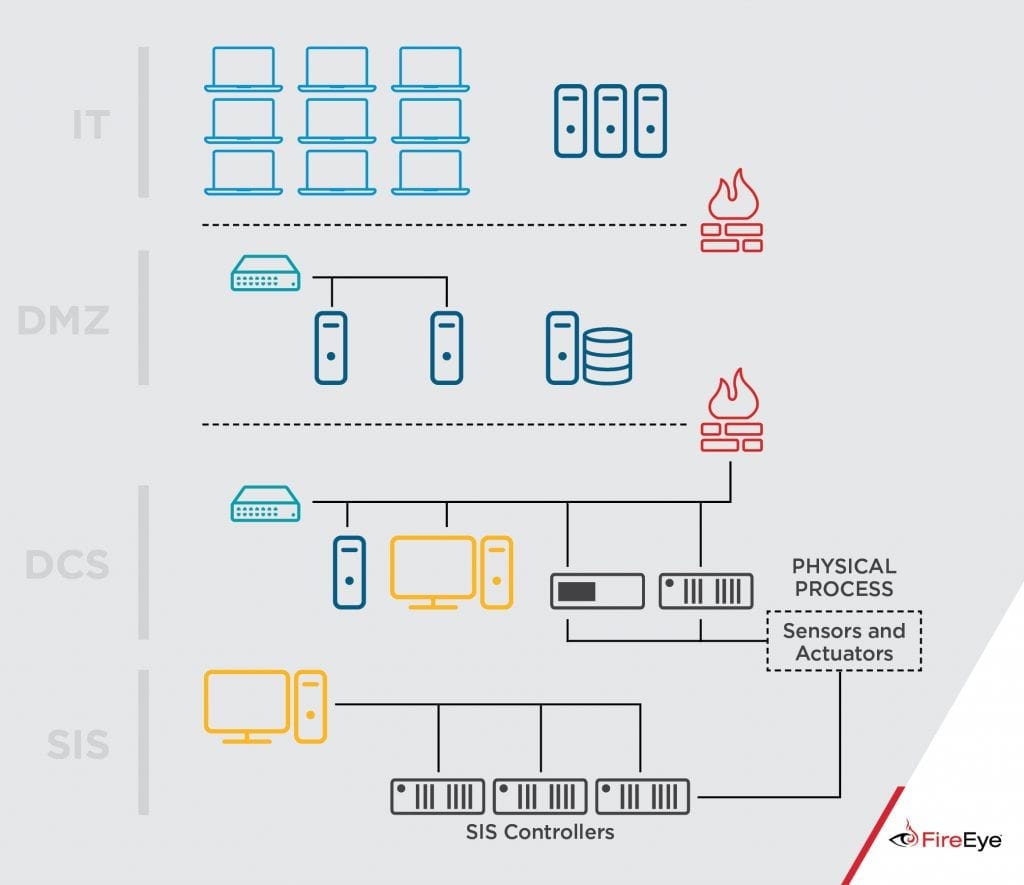
To get their intentions, the hackers used a malware called Triton, which was discovered only after a crash, which led to the shutdown of production of that structure. This malware is in practice of a framework that has been developed to interact with Triconex Safety Instrumented System (SIS) controllers responsible for industrial processes. When it tried to rewrite a security controller (SIS controllers), incorrect values were displayed, which caused the system to shut down due to security protection. As you can see from the following diagram, hackers have been able to hack security mechanisms and access SIS controllers. The area called Distributed Control System (DCS), in addition to allowing the interaction of sensors and actuators with SIS controllers, also allows remote access for monitoring and control of industrial processes. For remote access, the workstations of the engineers, which are located in the IT zone (the internal network zone and not exposed directly to the outside), are usually used and it was from a machine that was triggered the attack.
Components of the attack
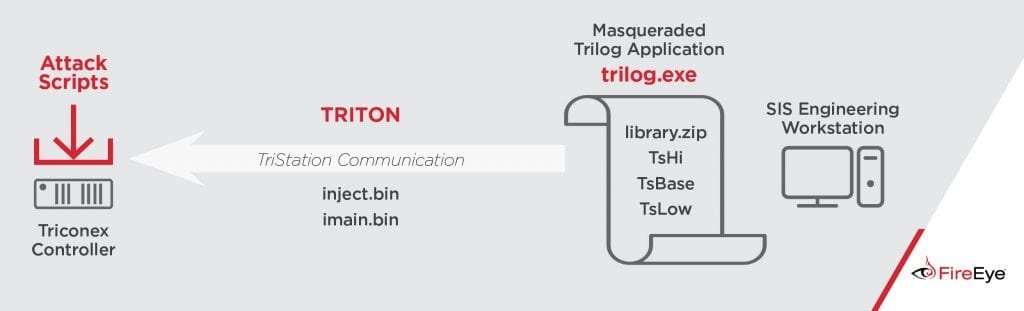
As mentioned, the TRITON malware was installed on a machine of an engineer who had Windows as the operating system. The malware was thus baptized to be confused with the legitimate app that is called Triconex Trilog. This application is used to evaluate logs and is part of the TriStation toolkit. The malware consists of a python script, transformed into an executable that makes use of the communications stack, rather than the TriStation protocol, which is used for configuring SIS controllers. Inside the .exe (trilog.exe we can find a set of libraries, TsHi, TsBase and TsLow). TsHi is a high-level interface that allows attackers to operate the attack using the TRITON framework. TsBase is a module that contains the function that invokes TsHiT and that in practice “decodes” the intentions of the attacker into functions that make use of the TriStation protocol. Finally, TsLow is an additional communication module that makes use of the UDP transport protocol. This module allows you to evaluate the connectivity to the SIS controllers, being able to discover the IPs of the same, using the function detect_ip. To do this, it uses the ICMP protocol. Along with an executable, there are still two binary files, inject.bin (file with malware) and imain.bin (with the “manipulated” control logic).
This type of attack has a clear intention, as in the past has been seen in other cases, and access to strategic information which is confidential may be part of a much more destructive goal. There are those who say that these first attacks try to test the tools and even see if they can learn by themselves. So, what do you think about this? Simply share your views and thoughts in the comment section below.
Δ